If your business is depending on the cloud, then security should be top priority. The fact that you are using the cloud provides another opening through which hackers can penetrate and wreak havoc to your cloud infrastructure. It is essential to your business to perform periodic security tests to assure that your cloud eco-system is secure from hackers.
What Is Penetration Testing
A penetration test is a cybersecurity test that includes automated and manual techniques that follow industry frameworks to identify and exploit security vulnerabilities like a hacker within your network infrastructure.
Commonly confused with other methods used to find vulnerabilities that include a vulnerability scan, compliance audit, or security assessment, the penetration test goes beyond by exploring multiple paths of an attack across different systems.
Why Perform Penetration Testing
It is worth the investment to perform the test because it identifies:
- Vectors that are open to attack.
- Analyzes low-risk vulnerabilities to pinpoint higher-risk ones.
- Highlights vulnerabilities that are difficult to find with automated networks or scanning software.
- Analyzes the impact of an attack.
- Tests your network’s ability to defend against an attack.
- Gather evidence to determine if it is worth spending more money on more security personnel and technology to defeat attacks.
- Ensures that your company is meeting compliance regulations.
- Provides your company with data about the path used to gain access into your network. In other words, the test assists in re-creating an attack chain or confirms that new security controls can defeat a future attack.
Cloud Penetration Testing
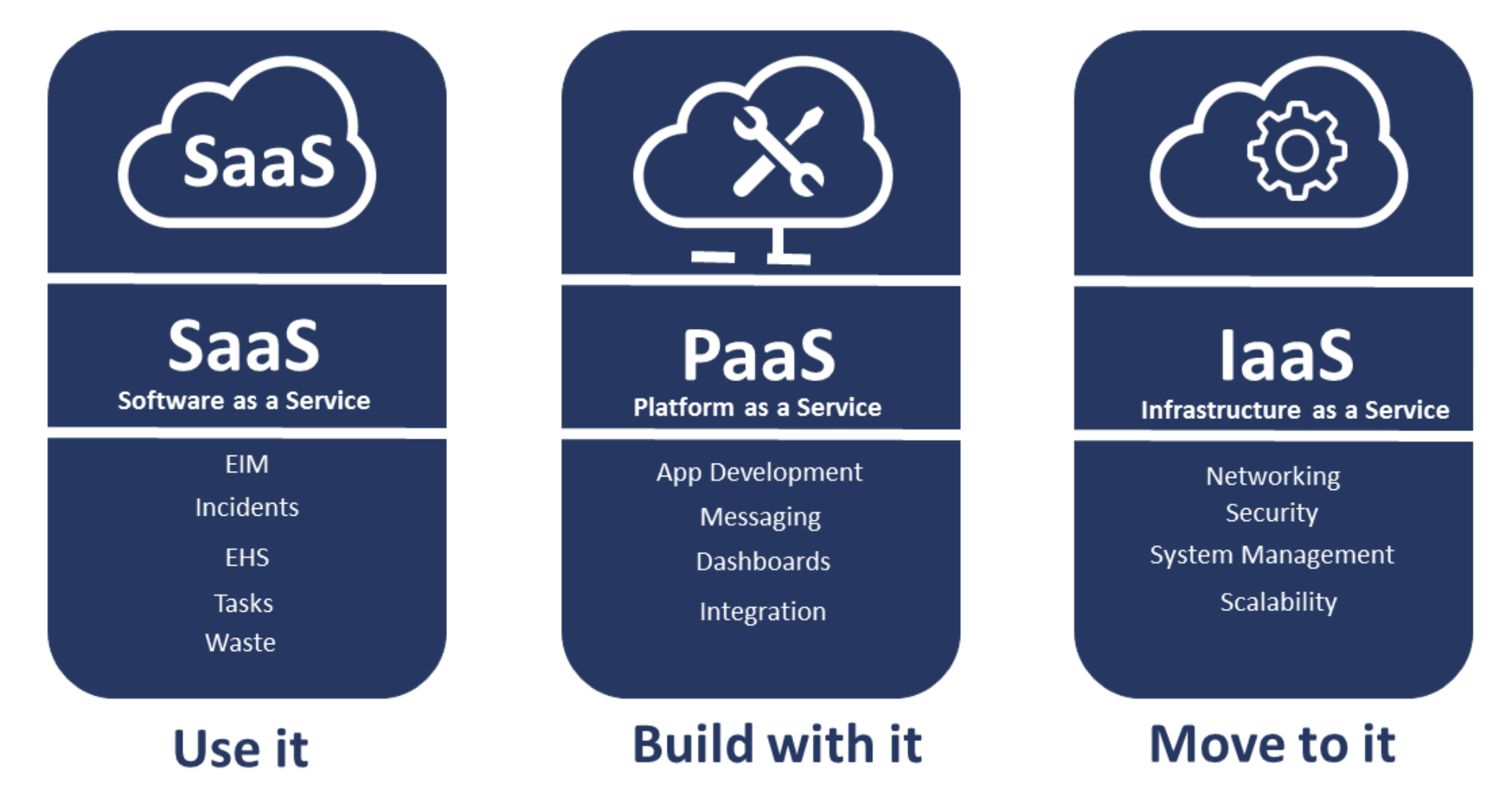
If your business is utilizing a cloud, then it is leasing infrastructure from a service provider through one of three models –- infrastructure as a service, platform as a service, or software as a service.
In the case of infrastructure as a service (IaaS), the machine and everything on it is under the control of your company and you can test everything up to the hypervisor.
In the case of a platform as a service (PaaS), the provider supplies everything one would need for an application including databases. Other companies and individuals, known as tenants are sharing the platform and a penetration test can adversely affect them.
Software as a service (SaaS) is a turnkey alternative that does not provide an opportunity for testing. You can, however, examine the application interface and API key management.
When doing a cloud penetration test on an infrastructure as a service or platform as a service, ask the provider about the type of equipment and architecture they are using, their security policy, patch management, and hardening or security audit protocol.
Who Does The Cloud Based Penetration Testing
You will need to determine who does the cloud based penetration testing. There are three alternatives –- the service provider, a third party, or your company’s IT staff.
If your service provider has the capability of doing the test, then you can use their testing calculations for your own audits. Moreover, if you aren’t capable of performing the test, then you might be able to get detailed audit reports from your provider. However, many in the trade suggest that you either have your in-house IT staff, if you have one, or a third party perform the test. This assure that information security tests are tailored to your cybersecurity needs.
AWS Penetration Testing
One of the most popular cloud platforms, Amazon Web Services (AWS), offers a number of cloud hosting services including compute and storage, content delivery, security management, network infrastructure, and in-house hosting for companies.
It offers the three models of cloud service –- IaaS, PaaS and SaaS.
You can’t perform AWS Penetration Testing on all service models. However, you can perform AWS Penetration Testing for the IaaS mode. That’s because the model is operated on your company’s premises. Therefore, you can perform penetration testing on so-called “user-operated services.” This includes cloud features established and organized by the user. It should be noted that the AWS cloud utilizes elastic cloud computing that the provider tests.
Your side of the network can pentest certain features including application programming interfaces, web and mobile applications, application servers and associated stacks, as well as virtual machines and operating systems hosted on your company’s premises.
Notify The Provider And Preliminary Planning
Prior to performing the cloud penetration testing it is advised that you notify the service provider. You will be required to fill out a penetration testing request form; and tell the provider the dates that the testing will take place, the IP address from which the testing is coming, and the scope of the IP address range being tested.
Your company should also define the extent of the test, decide the type of pentest to be performed (black box, white box, or gray box); and create a timeline in which the analysis, reports, possible repair of damage, and follow-up testing will be performed.
In conclusion, understand why the cloud penetration testing is being performed and what its objective are including the satisfaction of legal, regulatory and industry regulations.
