Have you ever heard of Quick UDP Internet Connections (QUIC) protocol for web browsing? I hadn't. It's kind of a User Datagram Protocol (UDP) implementation of Hyper Text Transfer Protocol (HTTP) and Secure HTTP (HTTPS).
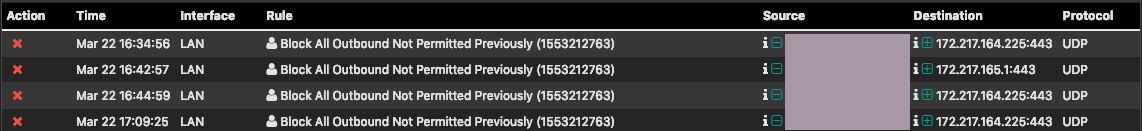
I'm creating a new course which will be hosted on Udemy about pfSense Firewall. In creating content for the course I configured egress filtering on my home network. I checked my logs to see what was being denied. I noticed UDP port 443 being blocked.
That's curious. I've been doing networking for some time and have never heard of anything standard operating on UDP 443.
According to a Google search, UDP 443 is QUIC protocol. The Chrome Browser will apparently use this as an option over HTTPS which is connection oriented. UDP offers some speed and performance benefits over HTTP which is connection oriented.
Each HTTP or HTTPS connection requires a significant amount of overhead compared to UDP or QUIC which are connectionless.
While I like the idea of a more efficient protocol, provided ways to verify everything is received where it is important to do so, there's a security issue yet to be addressed.
Our filtering and Next Generation Firewalls are watching TCP Ports 80 and 443 (HTTP and HTTPS), and will completely miss traffic on UDP 80 or 443.
None of our filtering, payload detonation, or any other controls around HTTP and HTTPS will be working to manage QUIC unless they are aware of it and configured to be able to control it.
Ideally, vendors will become aware of QUIC and protect it as they do HTTP and HTTPS. Until that time, I believe the prudent course is to block QUIC, forcing the use of HTTP and HTTPS.
Here are some slides from a 2016 Black Hat presentation by Catherine (Kate) Pierce, and Carl Vincent (vyrus) about HTTP/2 and QUIC. It highlights some of the problems that have to be solved and some pro's and con's including security related issues with HTTP/2 and QUIC. Nice work Kate and vyrus!
