Almost every modern company has a wireless network implemented for its services, but what happens when that network becomes the target of a security breach? In most instances, it’s already too late by the time someone hacks your wireless network — so it’s in your best interest to invest in prevention with wireless network penetration testing.
What is a Wireless Network Penetration Testing?
Wireless network penetration testing helps you validate your organization's wireless security controls to establish the level of risk and degree of your wireless network’s susceptibility to attacks.
If you have security controls designed to protect your wireless networks; penetration testing serves as a sparring partner for those controls. At some point, your security will encounter a fight for unwanted access, and every fighter needs a robust sparring partner.
We live in a world where wireless connections run everything. Through laptops, phones, and tablets; data flows from person to person through veiled communications.
Most corporations now have at the least, some form of a wireless network implemented for their operations. During this implementation, network segmentation, VLAN routing, and SSID controls need to be configured and defined so users can access the network without the trouble of intruders attempting to gain access for nefarious reasons.
A wireless network makes the exchange of information convenient for its users. This convenience makes the system more vulnerable for an attack because cybercriminals can attack it remotely.
Using a strong wireless security solution is a great start to preventing data leakage and breaches to your network, but even the most sophisticated security platform needs an assessment of its vulnerabilities.
This is where penetration testing comes in to play for your network. So, what can you expect with this type of security assessment? There are several phases included in a penetration test. Let's discuss what happens next.
Commonly, the assessment starts with the gathering of intelligence and information of your network, which will generate a heat-map and track the wireless signal being transmitted. Information such as the number of SSIS's being broadcasted, the hardware used, and the WiFi configuration of your network is gathered and documented.
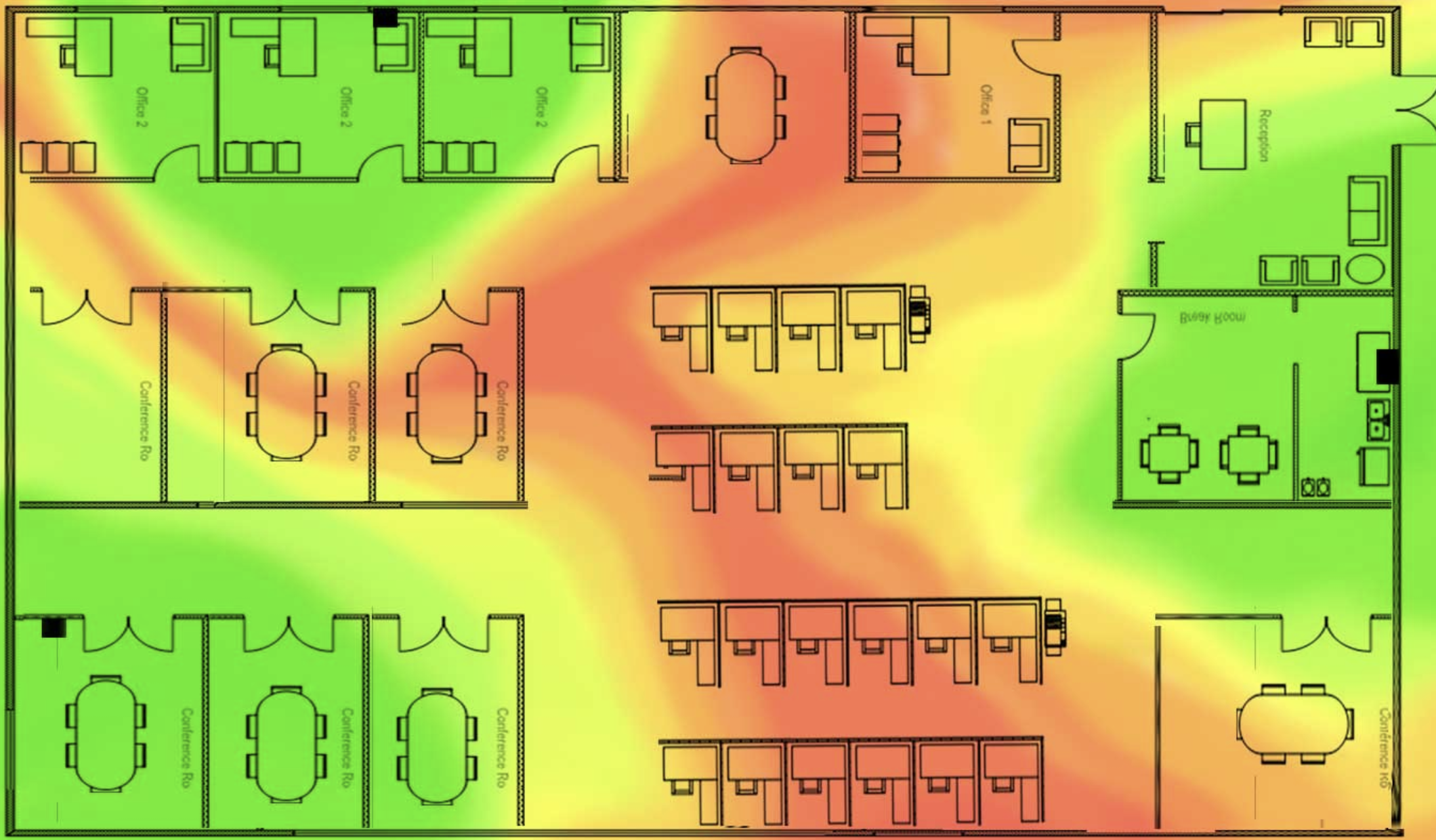
For example, think about our fighter getting ready for their sparring session. The sparring partner needs to know all the information possible about the fighter so they can test that fighter appropriately before the big fight. Practice makes perfect.
Now back to your network
Based on the hardware detected, the next step in the process is called “threat modeling” which determines which threats your network is most likely to experience. The tester then determines what is and isn't detectable in the wireless infrastructure. The assessment uncovers if there are any printers or computers detectable and if any files are open for sharing across the WiFi network.
Now the fight between your security controls and its sparring partner (penetration testing) is just starting to heat up. The pentester will evaluate all the information gathered to determine whether or not any vulnerabilities exist within the network. If there are vulnerable spots found, those weak spots are then exploited by the tester to the point where the network is breached.
Now you may be asking yourself, why would you pay someone to breach your wireless network? The same reason why a sparring partner might expose a defensive flaw in a training fighter; it's better to be knocked out in practice than in the championship fight.
Exploiting the vulnerable areas in your wireless network is necessary because the point of testing is to discover the holes in your armor so they can be repaired and ready for future attacks.
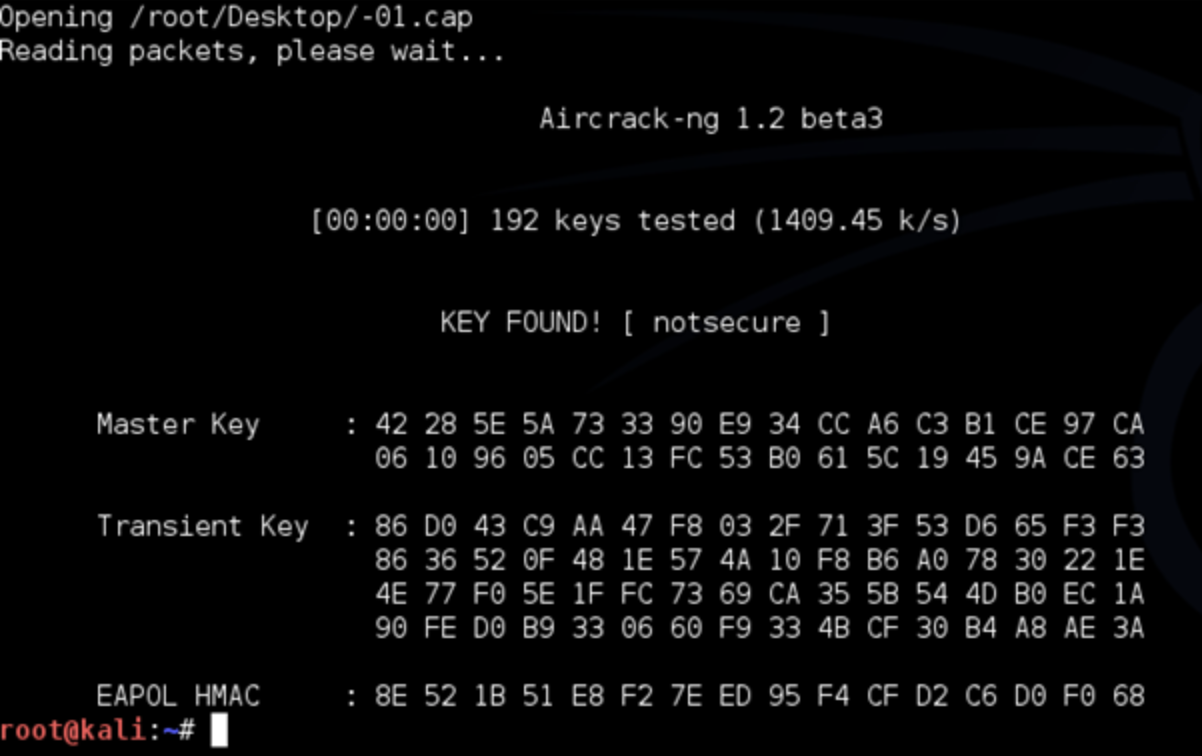
Once the penetration is concluded, and all gaps are exploited to the furthest extent, a report is generated which exhibits possible solutions that your IT department can use to bolster the security of your network. The executive report will be written in a non-technical language so those not familiar with specific terms can understand what needs to be done going forward.
Now your wireless security has been tested and is ready to fight any attack that may come along, but it's still not ready to send your fighter into the ring.
Once the proper adjustments are made to your network security, you should run another penetration test to see if the modifications are sufficient for long term security.
End Game
The most significant advantage in wireless network penetration testing is the consciousness of knowing where your information security faults rest. The first step to recovery is acceptance. You have to know where you're weak to grow. Knowing these issues sooner than later will save your company tons of money in the event your data is breached and compromised.
