A quick overview of OWASP and how it can help you secure your web applications.
I know most, if not all, full time security professionals have heard of OWASP and know some of the valuable tools and learning available there. I have run into many newly minted developers who have never heard of it though. That startles me, as I think web application security should be an important part of any web developer curriculum. This article is for you if you want to secure your web applications and haven't heard about OWASP yet.
There are many things you can learn or ways you can contribute to OWASP, but you'll likely want to get started by looking at their Projects.
In the menu on the left, select Projects to see a listing of current projects organized by maturity.
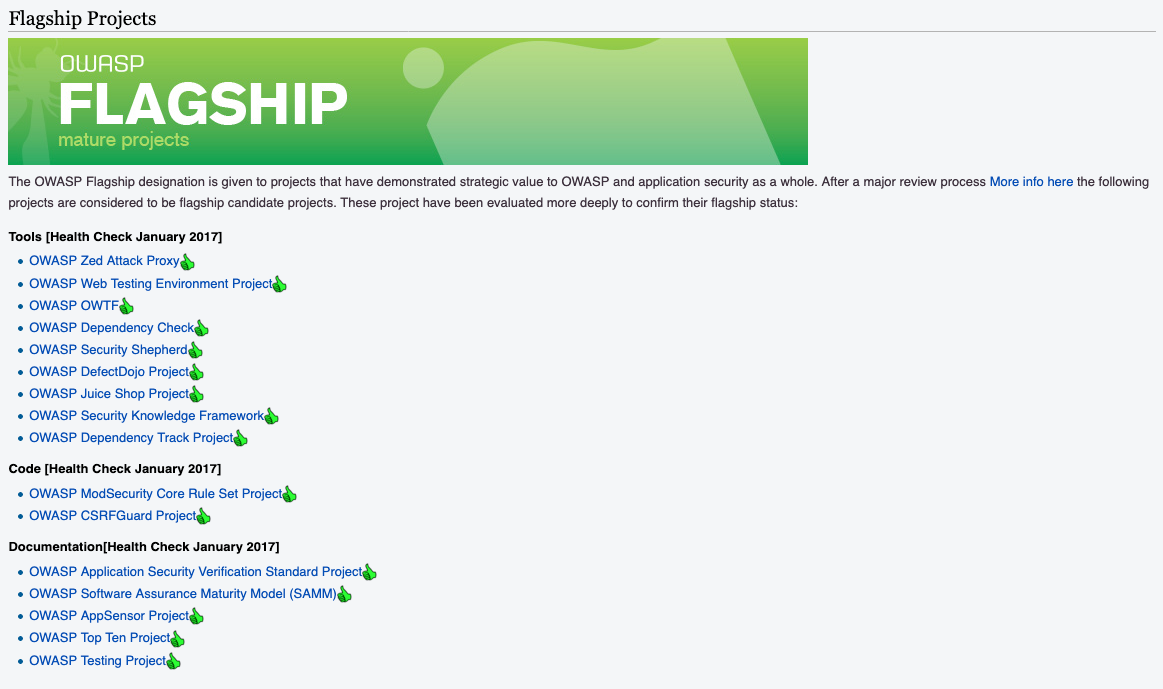
Flagship Projects are mature, widely used, and highly active projects. There's a bunch there, but I'm going to highlight a few of the ones I consider most useful. All are definitely worth a look though so please check out the site for other things you may find useful.
- OWASP Zed Attack Proxy (ZAP) - A full featured, free, open source web application security testing tool.
- OWASP ModSecurity Core Rule Set Project - The CRSP is all about keeping you up with the bad guys by keeping your Web Application Firewall's rules up to date.
- OWASP Top Ten Project - Stopping the top ten types of attacks will protect you from the vast majority of the risks that typically result in a compromise. Learn the top ten and how to prevent them here.
OWASP ZAP
ZAP has many videos and tutorials available including an overview video. It is available for Windows, Linux and MAC. It's even available via Homebrew for your MAC.
After installation, just find the ZAP icon to launch.

Of course, you may only run this against your own applications or those you have permission to scan. Otherwise, the law may come a knockin'.
I ran it against one of my own sites. borderroutersec.com.
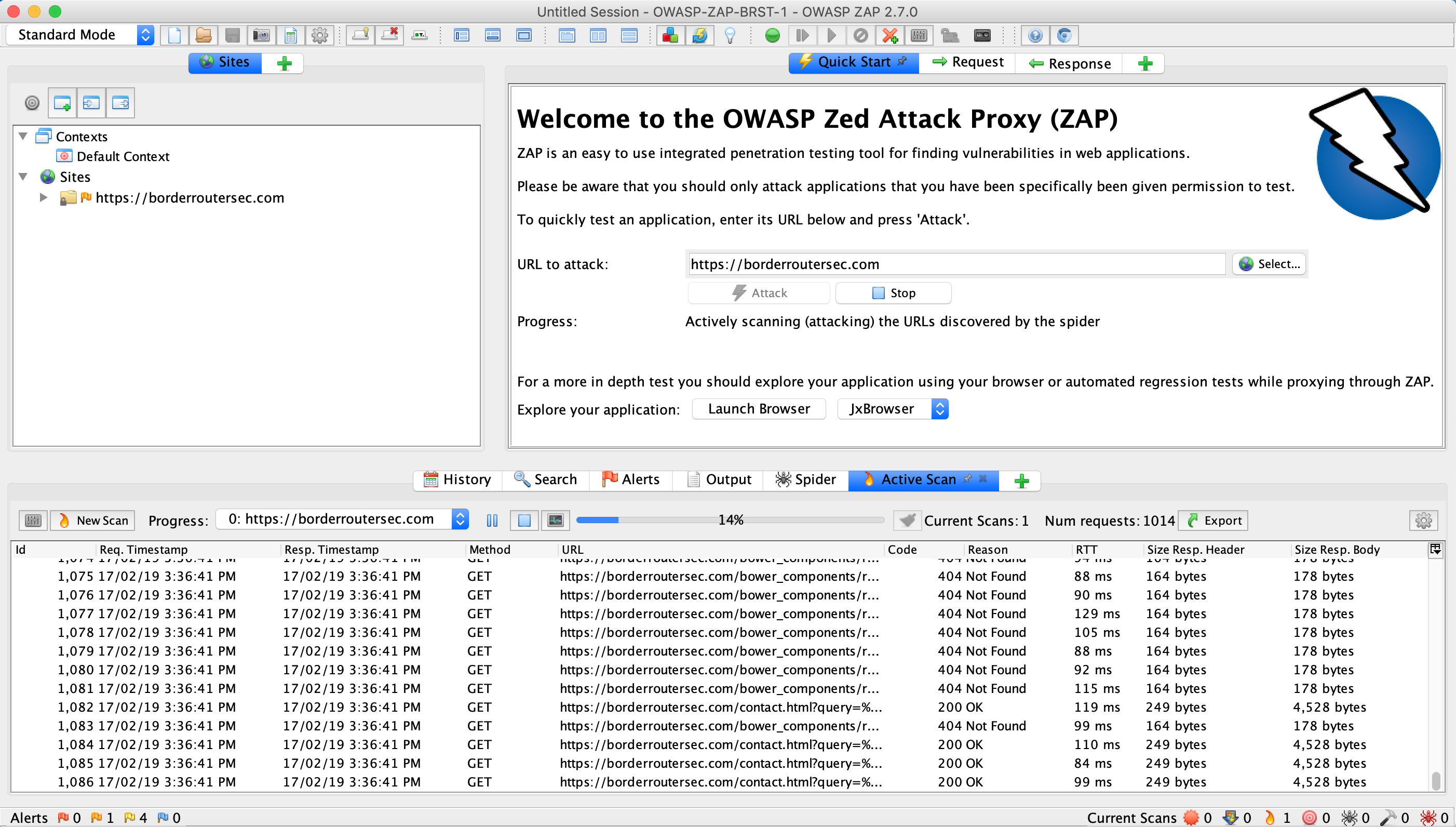
I had one Medium and four Low findings.
Of course, I'll use that information to up my security game on my own site. Pretty sweet!
If you'd like a vulnerable system to scan without risking jail time, you can try downloading Metasploitable. Whatever you do, don't expose your downloaded image to the Internet or any untrusted network when you fire it up. It will be hacked within minutes!
If you want to learn about web application security, ZAP is a great tool for you. Even for experienced penetration and web application testers with high priced tools available, ZAP is a nice addition to your tool kit.
There is a newer version of Metasploitable available from Rapid7 as a Docker Container, but it requires you to register to download it.
ModSecurity Core Rule Set Project (CSRP)
The ModSecurity project is an open source Web Application Firewall now maintained by Trustwave SpiderLabs.
A Web Application Firewall or WAF is similar in concept to a network firewall combined with an Intrusion Detection System/Intrusion Prevention System (IDS/IPS) for your web applications.
While you could certainly protect your web applications with a full fledged IDS/IPS like PFSense, a WAF is arguably more efficient and better at doing exactly what's needed to protect your web apps.
IDS/IPSs, and WAFs rely on rule sets, similar in concept to antivirus signatures for your antivirus software, to be effective. The bad guys are forever upping their game and trying to circumvent protections in the never ending arms race that is the Internet.
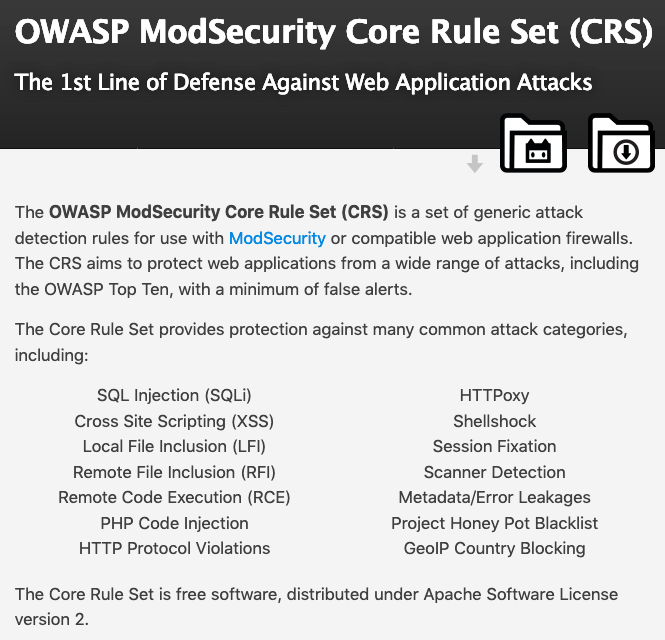
A world of talented volunteers is providing updates to the Core Rule Set used by many to provide a barrier between those on the Internet who would pone our servers and the servers themselves.
OWASP Top 10
Last but not least is the OWASP Top 10 list. Protecting your web application against these makes it much less likely your site will be hacked.

The list is updated every few years, but is usually just a slight shuffling of which types of vulnerabilities are seen the most or pose the greatest threat since the last list was published.
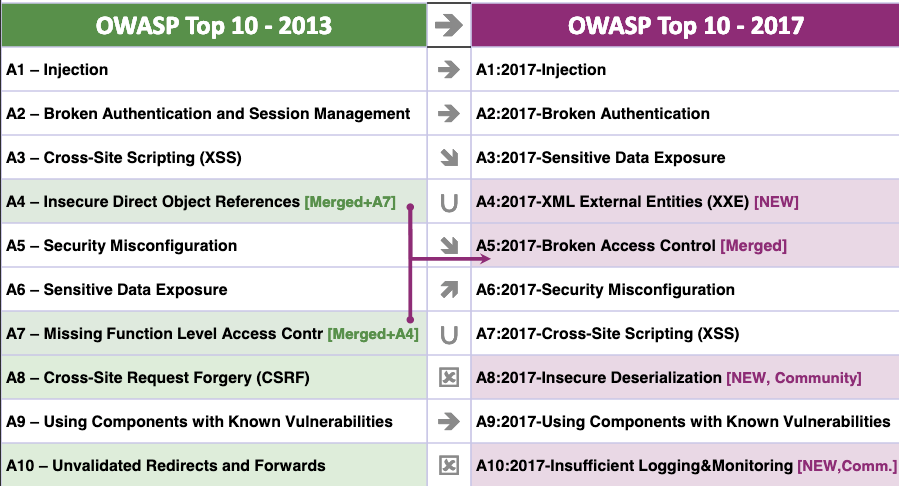

If you're a developer or security professional, you'll hopefully recognize many of these, understand why they're a threat, and know how to protect yourself from them.
We could all use a refresher or stand to sharpen our skills by digging a little deeper though. They're also a great resource to turn to for training people on common web application vulnerabilities and risk reduction.
Each vulnerability is broken down and explained systematically. We'll have a look at A1:2017, Injection.
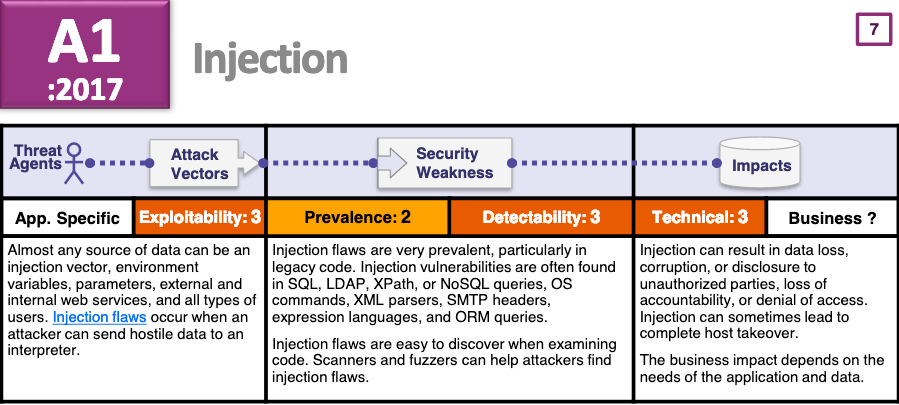
Threat agents searching for attack vectors find security weaknesses impacting the security of your systems.
In this case, threat agents can be internal or external: Anyone who can access your site and attempt to supply data to your web application.
If the input is not properly sanitized, it could be interpreted by a database or operating system and acted upon in ways the developers didn't anticipate.
The guide then helps you determine whether your application may be vulnerable.
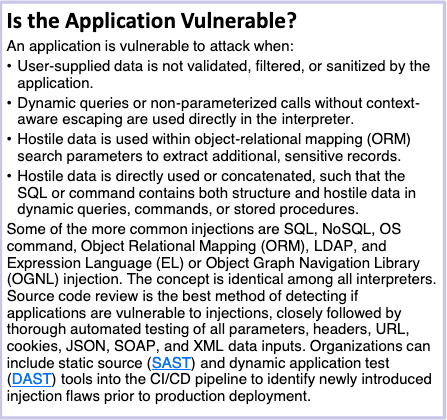
If your application:
- Receives user-supplied data that is not properly validated, filtered, or sanitized
- Performs dynamic queries or calls without context-aware escaping that is used directly by the interpreter
- The provided date is directly used to construct SQL commands or operating system calls
You may be vulnerable.
Next you'll learn how to protect your web application.

Some steps you can use to protect yourself include:
- Use a safe Application Program Interface (API) that only permits the activities you want
- Use positive or "whitelist" server-side validation of input
- Escape special characters
- Use SQL controls to help protect against SQL injection
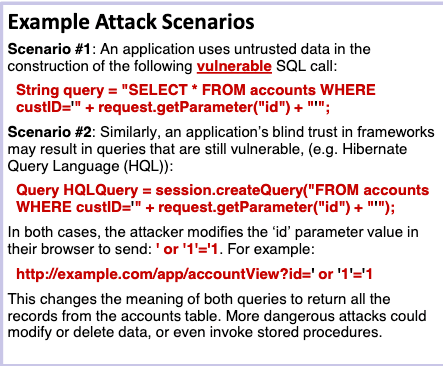
Next are some ways people may try to test for or exploit this weakness.
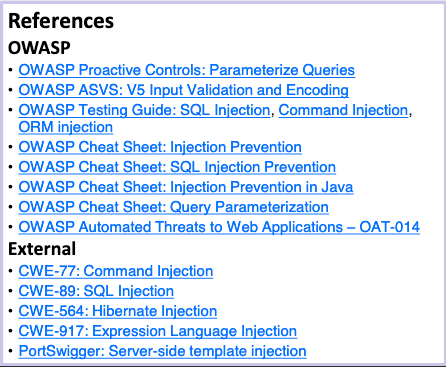
And finally, references for further reading.
There are so many talented people who want to teach you how to code securely and protect your web applications. Have a look around the site and see what you find useful.
If you want face to face meetings with security professionals, find the local OWASP Chapter nearest you. I attend events at the Toronto Chapter when I can. I know and respect many of the people who run it.
